Technically yes, but it’s very unlikely. There were vulnerabilities that allowed the retrieval of some information, but those have since been addressed. Hackers could deliver malicious apps through AirDrop, but recipients would need to configure their iPhone to run them and then run the malicious app.
Hi, I’m Aaron. I’m a security professional and researcher. I use and secure iPhones as part of my day job. Let’s dig into how AirDrop hacks work and why you’re unlikely to be impacted by one.
Table of Contents
Key Takeaways
- AirDrop creates a point-to-point device connection via Bluetooth.
- That connection can be used to gather limited personal information from a device.
- The connection can also be used to deliver malicious content to a device.
- You can protect yourself by turning off AirPlay when not in use and not accepting random AirPlay transmissions.
How AirDrop Hacks Work
AirDrop uses a proprietary communications protocol over WiFi and Bluetooth to transmit data between iOS devices. As long as another device is in range and has AirDrop enabled, you can transmit photos, text, files, and other data between devices.
What that means is that AirDrop, if active, transmits data about your iOS device in order to be able to be picked up by another iOS device. That can also be called an announcement. It also has open access to another device via AirDrop.
Those two vectors, announcement and open access, provide vectors for hacking. I’ll explain each in turn.
AirDrop Skimming
As highlighted above, the announcement involves displaying data about your phone via AirPlay. That information identifies you to other local AirPlay users.
It also needs to identify distinctive information for AirPlay to differentiate between similarly named devices. If there are two iPhones named Aaron’s iPhone in close proximity, there needs to be a way to tell to whom you’re sending information.
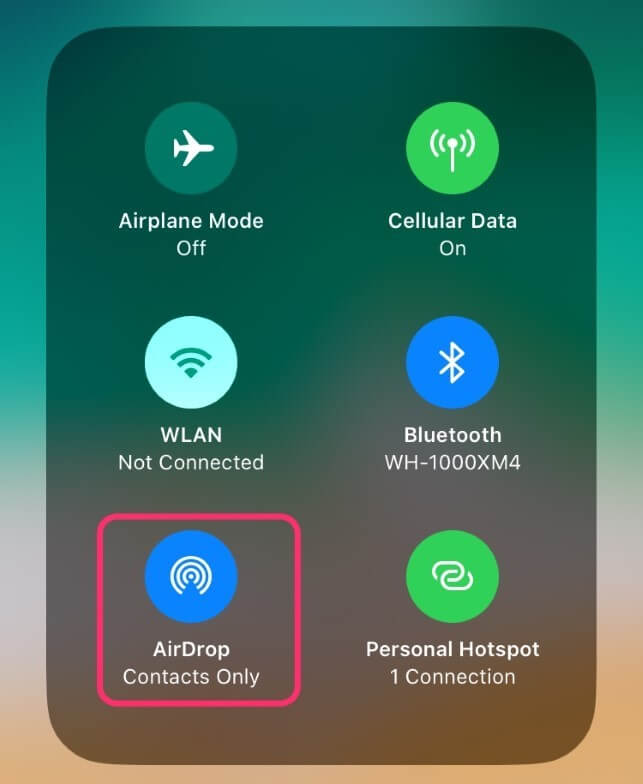
AirDrop handles this by defaulting to contact sharing. If a phone is in your contacts list, then it shares with that device. If it’s not, you need to enable that sharing.
To determine whether or not a phone is in your contacts, it verifies information with your contacts: phone number, email, and name. To be more accurate, the phone shares an identity hash comprised of some of that information. Once confirmed, it shares more of that information to verify.
Consequently, by spoofing that identity verification, someone can access some of your personal information. In fact, that vulnerability was identified as early as 2019. With that information, someone could spoof your phone in AirDrop or phish you, sending emails that demand money or information.
This kind of data gathering, where someone gathers information by spoofing a legitimate connection, is called skimming.
Alternatively, hackers could…
Transmit Files
AirDrop is ultimately a file transmission service. If you want to share something with someone, it’s a quick and easy way to do so if you’re in close proximity.
Hackers can take advantage of this. They can send you malicious code via pictures or files. When downloaded and opened, that malicious code could compromise your phone.
There are a lot of things that would have to go right for a hacker for that to happen. You would have to accept the file transmission. Then you would have to open the file. Your phone would have to be configured to launch the malicious code. Alternatively or additionally, your phone would have to be susceptible to a vulnerability leveraged by the malicious code.
In short, the right conditions would have to exist for this kind of attack to be successful. That’s not impossible, but there are things you can do to mitigate the attack’s success.
How to Protect Yourself
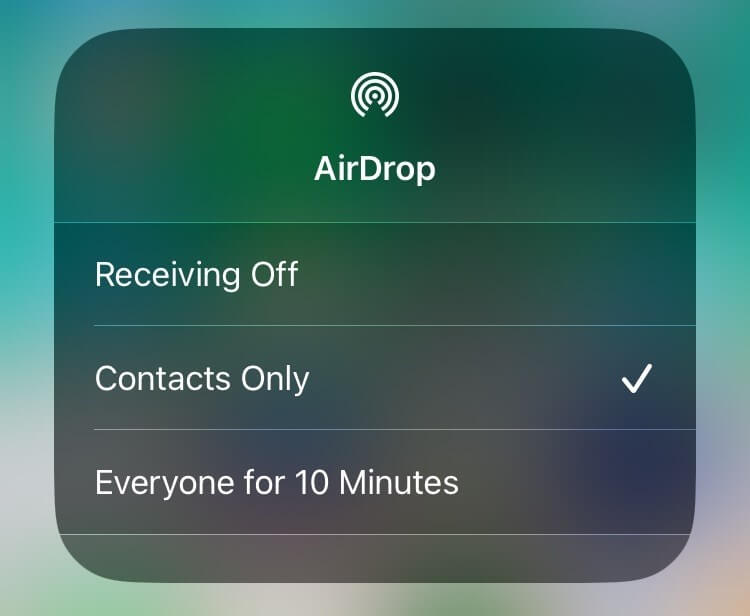
You can’t protect yourself from AirDrop skimming by turning off AirDrop when not in use. If your phone isn’t broadcasting for AirDrop, the personal information used to validate an AirDrop connection can’t be gathered.
To protect yourself from hacks from files received via AirDrop, don’t accept files unless you expect to receive a file and know the sender. Do not accept random AirDrop files.
If you have your AirDrop set to accept files from everyone, don’t. Change that setting immediately so you have to approve file receipt.
FAQs
Here are some answers to commonly asked questions related to AirDrop hacking.
Is It Safe to Accept AirDrop From Strangers?
No. Unless you know who’s sending the AirDrop or you expect to receive the AirDrop, don’t accept it.
What Happens if You Accept Someone’s AirDrop?
You’ll receive the file via the app from which it was sent. That could be Photos, the App Store, or other apps.
Why Would Someone Use AirDrop?
Someone would use AirDrop for close-range quick device-to-device transfers.
Conclusion
AirDrop is a very useful file transfer and sharing tool between iOS devices. Like most other technology tools, it’s not without its risks. Hackers can take advantage of the file transmission protocol to skim personal data or deliver malicious content. You can protect yourself, though, quickly and easily.
Have you ever received a file you didn’t expect via AirDrop? Let me know in the comments below!
